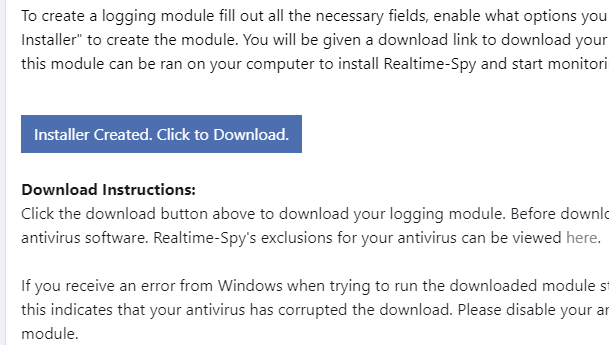
John the Ripper is probably the fastest, most versatile, and definitely one of the most popular password crackers available. It supports six different password hashing schemes that cover various flavors of Unix and the Windows LANMan hashes also known as NTLM (used by NT, 2000, and XP). It can use specialized wordlists or password rules based on character type and placement.
I got many Emails from my
blog readers requesting me to write an article on how to use john the ripper ,But actually there are may nice tuts on the net on this subject . So i taught instead of writing i can share one such article The following article is written by
Renegade
veersoni2010.blogspot.comJohn The Ripper TutorialI wrote this tutorial as best I could to try to explain to the newbie how to operate JTR. Remember, this is a newbie tutorial, so I wont go into detail with all of the features. JTR is a program that decyrpts Unix passwords using DES (Data
Encryption Standard).
The Process
Step 1: Download
JTR.Step 2: Extract JTR. In windows use winzip. In unix type tar -xzf john-1.6.tar.gz
Step 3: In windows open the command prompt. Go to the Start menu, click Run, type 'command' (no quotes) and press enter.
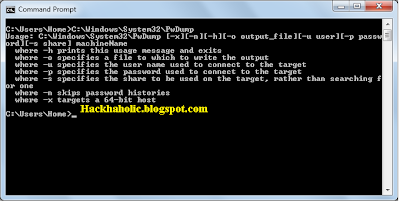
You with me? Good. Go to whatever directory to have JTR in. Type 'john' and press enter. A whole list of options will come up:
John the Ripper Version 1.6 Copyright (c) 1996-98 by Solar Designer
Usage: /WINDOWS/DESKTOP/JTR/JOHN-16/RUN/john [OPTIONS] [PASSWORD-FILES]
-single "single crack" mode
-wordfile:FILE -stdin wordlist mode, read words from FILE or stdin
-rules enable rules for wordlist mode
-incremental[:MODE] incremental mode [using section MODE]
-external:MODE external mode or word filter
-stdout[:LENGTH] no cracking, just write words to stdout
-restore[:FILE] restore an interrupted session [from FILE]
-session:FILE set session file name to FILE
-status[:FILE] print status of a session [from FILE]
-makechars:FILE make a charset, FILE will be overwritten
-show show cracked passwords
-test perform a benchmark
-users:[-]LOGIN|UID[,..] load this (these) user(s) only
-groups:[-]GID[,..] load users of this (these) group(s) only
-shells:[-]SHELL[,..] load users with this (these) shell(s) only
-salts:[-]COUNT load salts with at least COUNT passwords only
-format:NAME force ciphertext format NAME
(DES/BSDI/MD5/BF/AFS/LM)
-savemem:LEVEL enable memory saving, at LEVEL 1..3
You wont need most of these options. In fact, you don't really need any of these options. You can simply type 'john [filename]'. The filename must include the .txt extension. This is the regular crack. It will use bruteforce to decrypt all of the passwords in the file. If you're an impatient ass you can use a word list. This is not as effective but it's quicker (more on that later).
How to make a crackable file: Let's say that for some reason you have a DES
encrypted password but no file. If you want to crack it (why else would you be here?) you need to make your own file. Just create a text file and paste in the password. Now put a username (just any old name will do) in front of it with a colon separating the two. It should look something like this:
User:gyuJo098KkLy9
Save the file as crackme.txt (just an example) and go to the prompt and type 'john crackme.txt' (no quotes obviously). Now you just have to wait.
OptionsHere are a list of the options and what they do.
single: Single crack mode. This is only recommended for weak passwords as it includes only a few rules and a small wordlist.
Usage: john -single crackme.txt
wordfile: Uses a wordlist (basically a dictionary attack). What this does is tries every word in the list until it finds a match or you reach the end of the list. This is quicker than the default (bruteforce) attack, but I don't recommend this because it doesn't always find a match. More notes on wordlists below.
Usage: john -wordfile:password.lst crackme.txt
rules: Lets you define the rules for using wordlists. I don't use wordlists, so if you want to use this option I wont help you. Ok, ok, I'm just lazy. Shoot me.
incremental: I like this method. It allows you to do a bruteforce attack
under certain modes.
Usage: john -incremental:alpha crackme.txt (only letters)
john -incremental:digits crackme.txt (only numbers)
john -incremental:lanman crackme.txt (letters, numbers, and some special characters)
john -incremental:all crackme.txt (all characters)
external: This is a little complicated, so if you are lame don't mess with it. Basically this calls the options that are defined in the configuration settings. You can change these yourself, but I wouldn't recommend it unless you know what you're doing. No, I wont tell you how, go away.
Usage: john -external:[MODE] crackme.txt (replace MODE with whatever the
name of your mode is).
restore: Ok, let's say that you need to stop the crack in the middle. Press crtl+break. A file will be created in the JTR directory named 'restore' (no quotes doofus, and yes, no file extentionfilename.
Usage: john -restore:restore
session: Use this if you know that you will have to stop JTR in the middle of a crack. It allows you to create a new file that holds the data of your session. You can then restore your session later.
Usage: john -session:[save to filename] crackme.txt
status: Shows how far you got before stoping a crack (provided you used the -session option).
Usage: john -status:[filename]
show: Shows how many passwords have been cracked in a file and how many are left.
Usage: john -show crackme.txt
test: Shows how fast JTR will work on your computer.
Usage: john -test
users: Cracks the password only for the user or users you tell it to.
Usage: john -users:User crackme.txt
groups: Cracks the passwords only for the group or groups you tell it to.
Usage: john -group:lamers crackme.txt
shells: Cracks the passwords only for the shell or shells you tell it to.
Usage: john -shells:shelly crackme.txt
salts: Cracks the salts that have at least the number of passwords you specify.
Usage: john -salts:2 crackme.txt
format: JTR can decrypt many from many different formats, not just DES (but this is the most widely used one). Use this to force JTR to try a certain format.
Usage: john -format:DES crackme.txt (force DES)
john -format:BSDI crackme.txt (force BSDI)
john -format:MD5 crackme.txt (force MD5)
john -format:BF crackme.txt (force BF)
john -format:AFS crackme.txt (force AFS)
john -format:LM crackme.txt (force LM)
savemem: this tells JTR to automatically save your process at whatever
level you specify from one to three.
Usage: john -savemem:1 crackme.txt (save at level 1)
john -savemem:2 crackme.txt (save at level 2)
john -savemem:3 crackme.txt (save at level 3)
How to use a wordlist with JTR: I'll assume you already have a wordlist in the JTR directory (it comes with password.lst, if you want to make your own I'll tell you how later). Go to the prompt and type 'john -wordfile:password.lst crackme.txt' (no quotes, damnit). If the password is in the wordlist, it will work. Otherwise, you deserve it for using a wordlist when you have bruteforce capabilities, shame on you.
How to create a wordlist to use with JTR: First I will include a few lines of the wordlist supplied with JTR:
#!comment: Common passwords, compiled by Solar Designer.
12345
abc123
password
passwd
123456
The top line is a comment (duh). If you want to make a comment in your wordlist just follow the example. The other lines are passwords that the program will try when you use the wordlist. Put each password on a new line. In the event that you are too lazy to write your own wordlist you can download one (once again, I'm far too lazy to give you a link). It may or may not already be the right file format (.lst). If it isn't, just go to the prompt. Assuming the filename is lazy.txt, type 'rename lazy.txt lazy.lst'
Piping Output: Remember the -show option? You can get JTR to save that
output to a file. Just type 'john -show crackme.txt > crackinfo.txt'
There's my guide. I have an FAQ below:Q: Can I mix options?A: Yes, certain options can be mixed. You can mix options as long asthey don't clash. Play around with it a while.
Q: What does "Loaded 0 passwords" mean?A: There was a problem with either your password file or the syntax of your command. If you force BF decryption when your file has DES
encryption it wont work. If your password file isn't made right it wont work.
Q: What does "Password files required, but none specified" mean?A: Can you read? You can't just tell JTR to crack, you need to give it a file.
Q: What does "Unknown cyphertext format name requested" mean?A: When you use the -format option you need to check that you typed the name of the format correctly.
Q: How come when I typed 'john -users: login|uid crackme.txt' (which by the way is the usage shown in the list of option by JTR) I received this error:Option requires a parameter: "-users:"Bad command or file nameA: The piping symbol you used (|) can mean two different things. In this case in means 'or'. You're supposed to use login OR uid. When you type it in a dos window, you are running two separate commands.
Q: Can I speed up the bruteforce?A: Sure, just toss that old ass box of yours and get a new one.
Source - osix.net